Ransomware is a term that strikes fear into business owners and IT teams, and rightfully so. “In Q3 2020, ransomware attacks have increased globally by 40% to 199.7 million cases. [source]” But why exactly have these attacks increased so much? The answer is simpler than you might think, and it all goes back to ransomware-as-a-service.
Ransomware-as-a-service is a subscription-based model that works similarly to saas, or software-as-a-service. Essentially, ransomware developers will create a ransomware tool, and they will lease that tool to individuals that pay money to use the ransomware they created. In the past, hackers needed to have some coding experience to be able to successfully target and hack vulnerable systems, but with the implementation of ransomware-as-a-service, people with little to no technical experience can launch massive cyber attacks with ease.
How does it work?
For the raas model to work there are a few components that need to be in place:
- Expert-coded ransomware developed by ransomware experts (the individuals that design this software need to be reputable individuals in the ransomware space to generate outside interest)
- Monthly subscription for a flat fee
- One-time licensing fee with no profit sharing
- Pure profit sharing
Once someone has enrolled in the program, they are onboarded with documentation that contains step-by-step instructions on how to use the ransomware for coordinated attacks. There are even some ransomware providers that provide affiliates with a dashboard solution that helps them monitor how the ransomware is working. Crazy, right? It gets crazier. To recruit these affiliates, ransomware providers will post their tools on the dark web. From there, interested buyers can read through user reviews, view screenshots of the tool and then ultimately purchase the tool with the use of cryptocurrency, like Bitcoin.
How do the attacks work?
Most ransomware attacks are through phishing scams. Phishing is the method of stealing sensitive data through a seemingly innocent source- most of the time through email scams. When an unsuspecting party clicks on links from a phishing email, they expose part of their network to the hacker, which then leads to the penetration of their entire network. Once the attack has been executed, the extortion begins. Hackers will send a .txt file to the victim’s computer informing them that their information has been encrypted along with a ransom fee to obtain the files- like the image below.
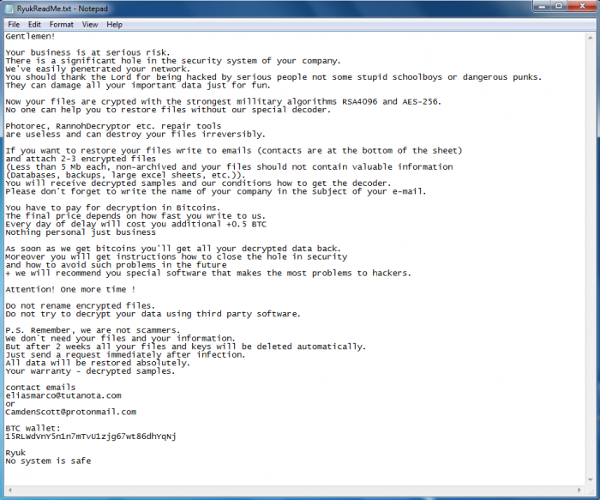
What can I do to keep my network safe?
This might sound obvious, but the best possible thing you can do to protect your network is to NEVER click on links from unknown sources. This is easier said than done because some of these phishing emails will try to replicate someone within your organization. However, they will not have the same email address, which is the number one red flag to look out for if you are unsure of where the source of an email is coming from. Another important practice to prevent ransomware attacks is to keep strong passwords that have multiple special characters and numbers and to repeatedly change passwords once a quarter.
Conclusion
Unfortunately, ransomware is here to stay. There are always going to be nefarious actors looking to exploit security, and that is why it is so crucial to have strong cybersecurity systems in place. Fortunately, Compulink offers state-of-the-art security solutions and services. If you are concerned about your business’ IT security, contact a sales team member for a free consultation, and we will help reinforce you network and ensure you and your business are protected.




