Every business and organization is different. You must factor in company/organizational size, your industry, unique regulatory and compliance requirements and other factors. Each business must manage their IT procurement in a way that fulfills its needs and respects its constraints.
This reality is felt across the IT hardware (e.g. devices, routers, servers), software (e.g. apps or licensed software) and services (e.g. cloud) you could procure.
Thus, a correctly designed and implemented IT procurement effort is vital to maximizing the value of your spending. The failure to do so will be felt beyond just your IT, but in your business or organization’s core activities.
We review the industry’s best practices for IT procurement. We also examine how you could benefit from IT procurement and overcome its challenges.
IT Procurement Best Practices
IT procurement specialists must strike a balance between cost savings and meeting organizational needs. Below is a list of goals that they seek to achieve during the process.
1. Acquire Technology That Aligns With Organizational Needs
All too often, technology purchases are made in the hope that the cost value will be worth the trouble of the organization having to adapt to the equipment.
In fact, the reverse is true; the acquired technology should be strategically procured so that it fits in with and supports business goals. Having to engineer workarounds and modify your IT environment — or larger processes or workflows — can lead to both inefficiencies and integration problems.
2. Forming Strategic Relationships
Forging a close relationship with specific vendors and/or IT providers offer numerous advantages to the IT procurement process. Not only will this result in cost savings by leveraging economies of scale and established logistical practices, but the right provider can also help to:
- Resolve adoption problems more efficiently
- Eliminates rogue buying and integrates with existing ERP systems like SAP, PeopleSoft, Oracle, and more
- Allow for the establishment of service level standards and agreements
- Create a framework for both parties to work together to improve the relationship
3. Involve Stakeholders
As part of a strategic sourcing process that attempts to glean as much information as possible before making a purchase decision. It’s important that all relevant stakeholders are involved in the IT procurement process.
This will allow your procurement personnel to understand the organizational needs, budget, and how all the intended acquisitions will impact operations.
4. Minimize Risk
All asset acquisitions come with an element of inherent risk — and IT is no different. From technology that fails to support the company’s needs to potential financial or compliance issues down the road, a procurement specialist will work with risk mitigation and security in mind.
Some of these practices include:
- Conducting a full risk analysis
- Determining the probability of financial losses
- Roadmapping, planning for future projects, and implementing plans to reduce their impact
5. Acquire Assets With an Eye Toward The Future
Many organizations seek to lower their capital acquisition costs and therefore make purchasing decisions based on short-term needs and upfront price.
However, top companies choose to look at total cost of ownership when making acquisitions.
Instead of getting quotes from vendors, today’s IT procurement specialists, like those at Insight, will identify how much the technology will cost to operate and eventually dispose of; ensuring that the most cost-effective option is selected that will pay dividends over its lifespan.
Understand Your IT Infrastructure
Before approaching IT procurement, we must review the benefits and difficulties your company likely faces in managing its IT infrastructure. This is an important discussion because, ultimately, your IT procurement efforts are aimed at improving the effectiveness of your IT infrastructure.
Your IT infrastructure certainly includes at least two of these three core components: hardware, software and services. For most, hardware and software are a given (e.g. word processing from a laptop).
In today’s environment, IT infrastructures include more than simply computers and productivity applications. You also have networking infrastructure connecting your company to the web and internally between different computers, printers and on-premise servers.
Likewise, your productivity suite includes email which could be based on Exchange, Google or a proprietary suite as well as customer relationship management (CRM) and other apps.
It is when these systems age and lose relevance (with current as well as emerging trends and behaviours) that IT procurement becomes an issue.
Factors such as current hardware and/or software falling out of compliance, not having the right features, higher cost-of-ownership and others make IT procurement key.
The Difference Between Hardware and Software Procurement
What is Hardware Procurement?
In terms of hardware, your IT procurement efforts may focus on replacing aging laptops and/or workstations, routers, printers, mobile devices and in case of in-house or on-premise hosting servers.
What is Software Procurement?
Software procurement can include renewing licenses for productivity applications, e.g. Microsoft Office, Adobe Creative Suite, Citrix, etc. Instead of software-as-a-service (SaaS) solutions, you may also look to build custom applications. In-house development would also be procurement.
Your IT procurement process must fulfill your operational requirements. However, they must follow your compliance standards, meet your cyber security needs and drive strategic business goals (increasing profitability and market-share).
In effect, you will not have developed a sound IT procurement strategy if you fail to achieve all of your business or organization’s requirements (not just daily operations, but compliance too).
It would be a waste of resources otherwise, be it directly (through the purchase of the wrong or unwanted systems) or indirectly (resulting in underused or insufficient capacity).
What is an IT Procurement Process?
The IT procurement process is the combination of numerous tasks and responsibilities, namely:
- defining your IT requirements,
- managing vendors, negotiating and implementing your contracts,
- existing asset management
- and verifying the quality of products and services provided.
Every business and organization must have a clearly defined IT procurement strategy in place.
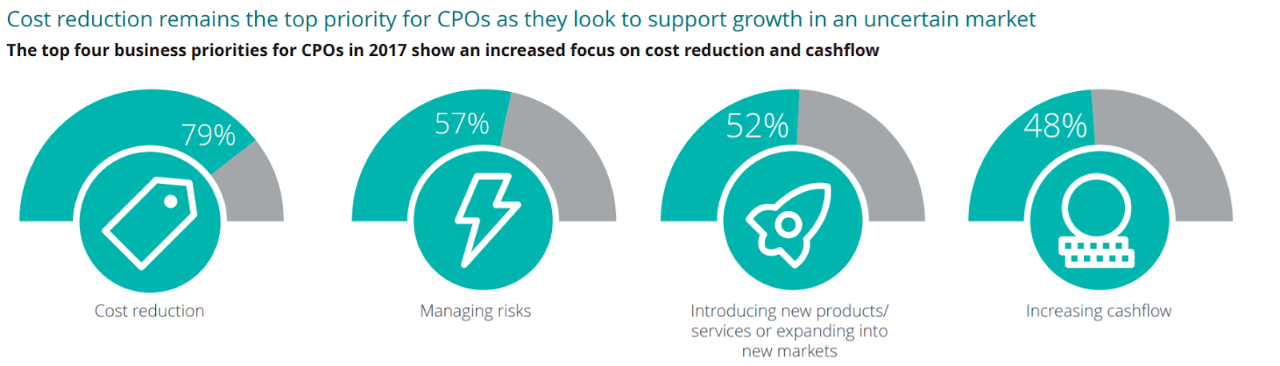
This is to ensure that IT procurement is done correctly and to secure internal stakeholder e.g. upper management support. The latter is important because business executives want to see IT as a driver for profitability instead of a costly overhead
You must demonstrate how IT procurement will help with reducing time spent on certain tasks, increase output and other net-revenue-focused goals. You must also show that the spending is essential and is being put towards solutions that generate maximum value.
The infographic below showcases how strong internal stakeholder support from executives is integral to IT procurement:

You must also stop excessive or unauthorized spending. The IT procurement strategy serves as a guard for preventing ‘maverick spend’ IT spending that occurs outside of your process.
Dark spending is also a threat as it undermines the trust upper management have in your IT. You risk looking like a black hole for money (i.e. a costly and cumbersome overhead).
You can prevent both maverick and dark spending by building accountability mechanisms (such as a system of approval) throughout your IT procurement process.
You could also separate the “buyers” from those in-need of systems (“requesters”). This ensures that the one requesting IT solutions can’t approve the sale for themselves on their own.
It’s also possible to prevent the conditions that lead to maverick and dark spending by selecting the right IT OEMs. Ensure (before the implementation phase) that your requirements are being met across every scenario (e.g. having a scheduled replenishment policy for printer cartridges).
IT Procurement Benefits
By implementing IT procurement best practices, you will leverage major improvements in both operations and strategic goals.
Operational Efficiency
With new hardware, recent software releases and/or IT services (e.g. cloud services), you can accelerate your daily operations.
For example, you could equip your sales representatives with new mobile apps connected to cloud-hosted databases. This lets your sales rep to input, view and manage data from the palm of their hand. At present, they might be pulling-up a laptop and manually connecting to the web, which consumes more time and effort.
Compliance & Security
IT procurement offers an opportunity to replace IT systems that don’t comply with your industry’s regulatory requirements. Doing so ensures that your organization is shielded from current and emerging cyber threats. These threats can cause extremely costly data breaches.
Similarly, ensuring that your IT system compliance and cyber security measures are up to par with current and upcoming regulatory standards shields you from expensive government fines.
You will notice that in most cases, compliance and cyber security are intertwined. Following one (in alignment with industry standards) should lead to following the other.
Security
This can include:
- replacing routers that aren’t equipped to support today’s encryption standards;
- moving your data to a cloud hosting provider that provides HIPAA-compliant encryption,
- on-site security and network monitoring services;
- and switching to up-to-date software builds.
Compliance
Businesses and organizations are beholden to government, industry and vendor compliance standards. For example, you can move your data to HIPAA-compliant data centers (available through public or private cloud-hosting providers) to ensure that your data is being managed in compliance with privacy regulations such as the General Data Protection Regulation (GDPR).
IT Procurement Challenges
It’s not easy to correctly implement a IT procurement strategy.
Negotiating with OEMs
In theory, you can negotiate with IT industry OEMs to secure favourable pricing, strong after-sale support and warranties. However, the practical side isn’t simple.
In terms of negotiating with OEMs, it’s best to have strong industry partnerships, e.g. Microsoft Gold Partner, Cisco Gold Partner, IBM Business Partner, etc. These partnerships are a sign of the OEM trusting you to implement their best practices (e.g. in configuration).
Such partners are in a better position than non-partners for understanding the OEM’s offerings and for negotiating favourable pricing, support and guarantees.
Internal Talent & Skill Gaps
Purchasing IT equipment is only one side of the IT procurement process. Your internal IT team must also have competency for properly implementing the strategy.
According to Deloitte’s study, “60% of CPOs still believe their teams lack sufficient capability to deliver their procurement strategy.” This is reflected in knowledge and training:
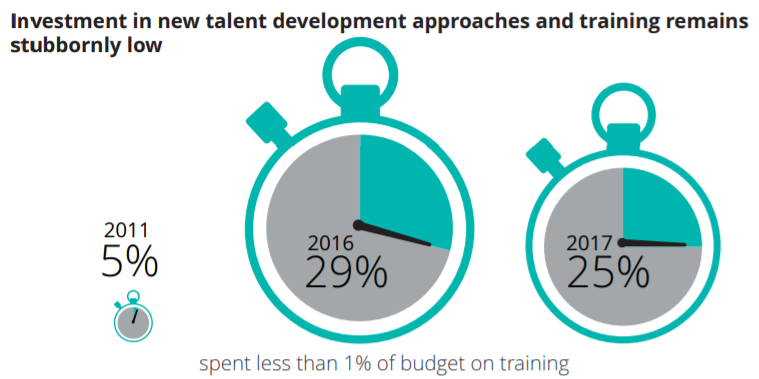
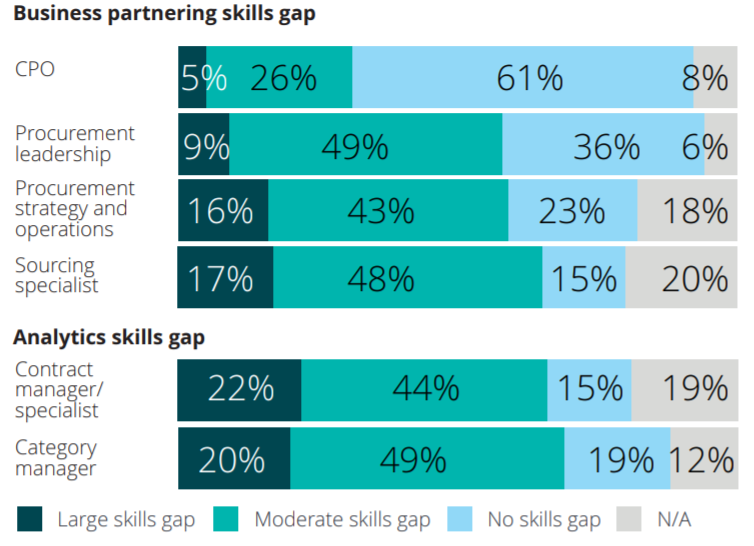
Businesses are reporting severe (e.g. 50%+) gaps in skills across many IT procurement areas, including procurement strategy and operations and sourcing.
Planning & Implementation
A big problem with internal knowledge gaps is that it weakens the planning and implementation phases of your IT procurement.
Basically, your IT procurement team might not have enough knowledge to properly identify your organization’s IT requirements. This could lead to improper purchasing, potentially needless or excessive spending (or, on the other hand, missing key requirements).
Implementation problems can include delays in receiving, installing, configuring and validating new IT systems. Likewise, your IT procurement team might not have incorporated enough or correct training for your company’s employees.
This besides trouble using new systems can open other problems, such as a lack of trust in new systems and sticking to the old.
Understanding IT Procurement Risks
There are many IT procurement risks. Many of them occur due to your IT procurement team not having enough knowledge and experience.
We’ve compiled a list of these risks below:
Incorrectly Defining Requirements
Your IT procurement team may understate or overstate your company’s IT needs in certain areas, e.g. procuring too many laptops or workstations and not enough software licenses.
In such cases, not only do you risk failing to meet your IT requirements, but you could end up with an inaccurate cost-estimate. Buying too many hardware systems will drive your costs up and lead to the waste of funds (procuring too little can result in a falsely-low figure).
Misinterpreting User Requirements
When there’s a knowledge gap, there’s a high risk of your team missing the mark on spotting the actual needs of your company.
For example, your sales team might require a CRM suite. However, your IT procurement team may select one that doesn’t have the features they need. In this case, the purchase will result in the loss of time, money and productivity across the board.
Insufficient Funding
You might have a strong IT procurement team, but they can’t do much good there isn’t enough money. The lack of funds generally leads to delays and, if you had already tendered but failed to procure, a reset of the tendering process.
Imagine your IT procurement team had already selected systems for your company and were close to signing a deal. Walking away from that deal may damage your reputation with IT OEMs.
Unrealistic Time Frame & Implementation Risks
Your IT procurement team might expect the supplier to deliver in a very short period of time.
Tight timelines might push many potential vendors away from your bid, reducing your options. You also risk implementation problems if the winning supplier is unable to deliver on those tight deadlines.
The supplier’s failure to deliver your IT systems on time will lead to delays at your end and set your IT programs back. In some situations, such as sales teams needing CRM, this can result in productivity drops.
Next Steps: Get Help in Building an IT Procurement Policy
You can prevent the challenges discussed above by incorporating IT procurement best practices into your IT procurement policy. Basically, you should anticipate these problems ahead of any IT procurement effort. In other words, you should prevent these problems from occurring.
This article was originaly published on Insight, click here to view the original article.